Predatory Journals

One of the challenges of publishing an open access (OA) journal is that OA has been used as a cover for fraudulent publications that promise researchers and scholars fast publication of their work for a fee. These publications are referred to as predatory journals because they prey on less experienced scholars and also provide an outlet to meet the ever-increasing publication requirements for scholars, researchers, and medical doctors for promotion (or, in many cases, simply keeping their jobs).
The economic models of open access journals can include subsidies provided by authors, called article processing charges (APCs); the offer of publication supported by APCs is not by itself an indication that a journal is fraudulent. However, two hallmarks of predatory publishing are pay-to-publish models with high APCs and a lack of rigorous (or any) peer-review. As Florence Cook, Roganie Govender, and Peter A. Brennan (2023) explained,
Predatory publishers, also known as counterfeit, deceptive, or fraudulent, are organisations that exploit the open-access scholarly model by charging hefty article processing charges (APCs), often without the scientific rigour and ethical processes offered by legitimate journals. ... Common characteristics include inappropriate marketing and misrepresentation of services by targeting individuals with solicitation emails, inadequate peer-review processes, lack of editorial services and transparency about APCs, and false claims about citation metrics and indexing that cannot be verified.
Such predatory publication venues are part of a larger ecology of fraudulent academic work that meet the needs (and perverse incentives) of academic and national assessment systems that value quantity of publication over quality. One of the other key players in this ecology are businesses known as paper mills:
Paper mills prey on the “publish or perish” culture prevalent in some parts of the world. Researchers in many regions are incentivized to publish as many articles as possible, with numbers of publications being used in funding and promotion decisions. Paper mill companies produce fake data and images, and compile these into manuscripts that researchers can buy authorship on, often paying a higher rate for first or corresponding author positions. (Fisher, Nugent, & Pendlebury, 2022)
In the past, these paper mills have employed writers to craft false publications, which can be submitted to legitimate journals or, for lower quality papers, can be published by predatory journals. There is a deep concern in the scientific community in particular that these kinds of publications are not only eroding public trust in science/research but are actively being used to support misinformation campaigns that can literally lead to mass casualties, as was the case with the proliferation of false Covid research (Teixera da Silva, 2020).
One of the earliest attempts to deal with predatory publishing was the publication of an assessment of journals using a series of markers (such as nonexistent or fake editorial boards, claims of excessively speedy peer-review, poorly designed websites) produced by librarian Jeffrey Beall. Known as Beall's List, it was ultimately taken down under legal threats from publishers who did not wish to be identified as (even just potentially) predatory. However, versions of the list can still be found on the Web, as the only successor to this model of tracking potentially bad actors is a list of acceptable and cautionary journals compiled by Cabells, which is only available to researchers if they have access to an institutional library that has purchased it (which leaves out the vast majority of scholars targeted by predatory journals).
Sometimes it is fairly easy to identify a fake article, and the inclusion of such articles may be an indication of predatory publishing practices. However, it may also simply highlight flaws in the editorial processes of legitimate journals, which are often pressured to produce more content at a faster rate, both in service of the massive profits of companies like Elsevier, Taylor and Francis, and MDPI and to accommodate the increasing demand for publication venues for scientists and researchers who need to show research productivity in order to progress in their careers.
Some researchers have taken to sending obviously false papers to journals; in cases where those papers are published, a fairly strong case can be made that the journal is likely predatory (particularly if the journal also features fake editorial board members and suspiciously fast peer-review processes). A notable example is provided by Renata Schiavo (2020), which documented a nonsense publication intentionally submitted to the Asian Journal of Medicine and Health (AJMAH):
According to a 2020 article published in the peer-reviewed journal AJMAH, the number of fatal accidents caused by push-scooters had increased dramatically in recent times. The paper also highlights another interesting fact: COVID-19 disease and accidents caused by push-scooters seem to have a lot in common. Quoting the words of the authors: “both can have deadly outcomes in which the patient might even die.” In light of such a strong similarity and given that the use of hydroxychloroquine has shown miraculous results in the treatment of COVID-19, the study concluded that the same drug may significantly help in decreasing deaths from push-scooters.
(Oddly, there are three peer-review reports, each of which appeared to take the manuscript seriously, despite the headnote that indicates that study three in the paper was completely imagined by one of the authors.)
An Activity Theory Approach to Understanding Predatory Publishing
One way to consider the effect of predatory publishing on the overall aim of academic research is through the lens of activity theory, which maps the main components of a particular activity. As Claire McAvinia explained,
Activity Theory (AT) proposes that any human activity can be described and analysed and that activities have a structure, are undertaken under certain conditions and mediated by particular tools, instruments or artefacts, and are performed to meet a purpose.
In its most basic form, AT sees activity as a subject interacting with an object to obtain a desired outcome (the throughline at the midpoint of the diagram below). The subject employs instruments (sometimes also listed as tools) to work on the object - these instruments might be embodied objects, such as hammers, computers, lasers, etc., or they might be more conceptual, like plans or brainstorming. In AT, activities are carried out in a social context (here expressed as "community"), which can be seen at the base of the triangle: Rules explain how subjects are expected to relate to the community and the division of labor shows how the community relates to the object. This framing can feel pretty abstract, but as we'll see, once we start filling in the details of a specific activity, these relationships and connections become easier to see.
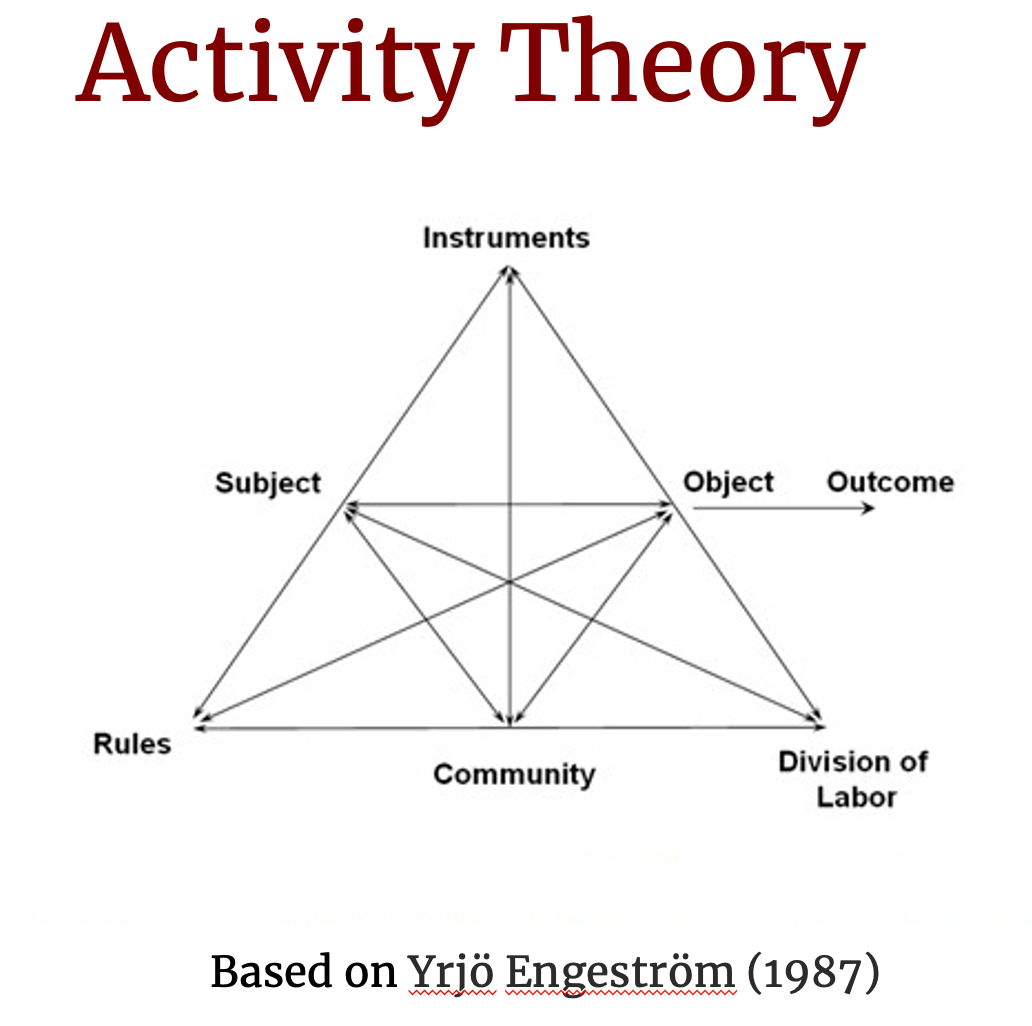
Now, I should note that I'm using here a very loose mapping of AT as a kind of big-picture approach; a full consideration of publishing as an activity would be much more complex (and, of course, AT has a lot more to it than just this model). But as a first step in comparing forms of a particular activity, I find this approach helpful.
If we apply our model to academic publication, we can see how each component contributes to the outcome (in this case, publication of peer-reviewed scholarship). We can build an AT model using the publication process as the subject (that which leads to the outcome), where we can identify the instruments that are necessary such as content knowledge, writing, writing tools used by authors, writing and editing tools used by editors, design tools used by authors and editors, publishing platforms, plagiarism detection tools, email, and so on—this is certainly an abbreviated list intended to capture the big-picture elements of the process.
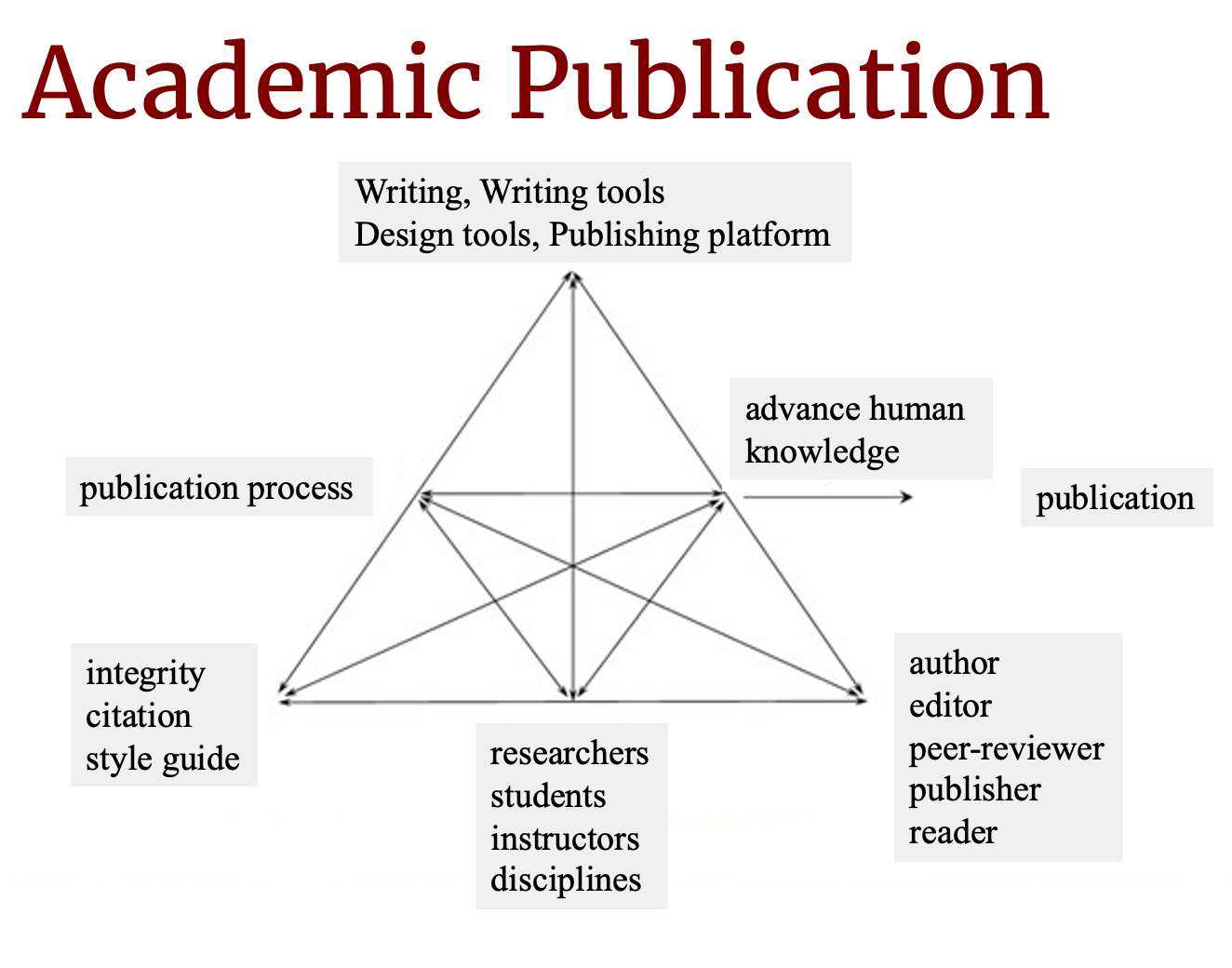
We also identify rules, such as maintaining ethics with regard to the work of others (i.e., don't plagiarize), enacted through citation rules and specific styles (e.g., APA or Chicago). Citation schema and style guides can also be instruments, so they can appear in both places, but to avoid clutter (and possible confusion), I'm placing them only in the rules section in this model.
The community that engages in this work is comprised of authors, publishers, and readers, but also includes the broader categories of researchers, students, instructors, fields, and disciplines. The division of labor occurs between the author, editor, peer-reviewers, publishers, and readers (although we could possibly add copyeditors, designers, and other roles depending on the kind of publication).
The object (why undertake this activity?) is purportedly, or perhaps ideally, to advance human knowledge. The outcome (what does all this activity produce?) is the publication.
But if we revise our model to focus on predatory publication specifically, we can see the changes that happen to the activity, most notably in the rules, instruments, and division of labor.
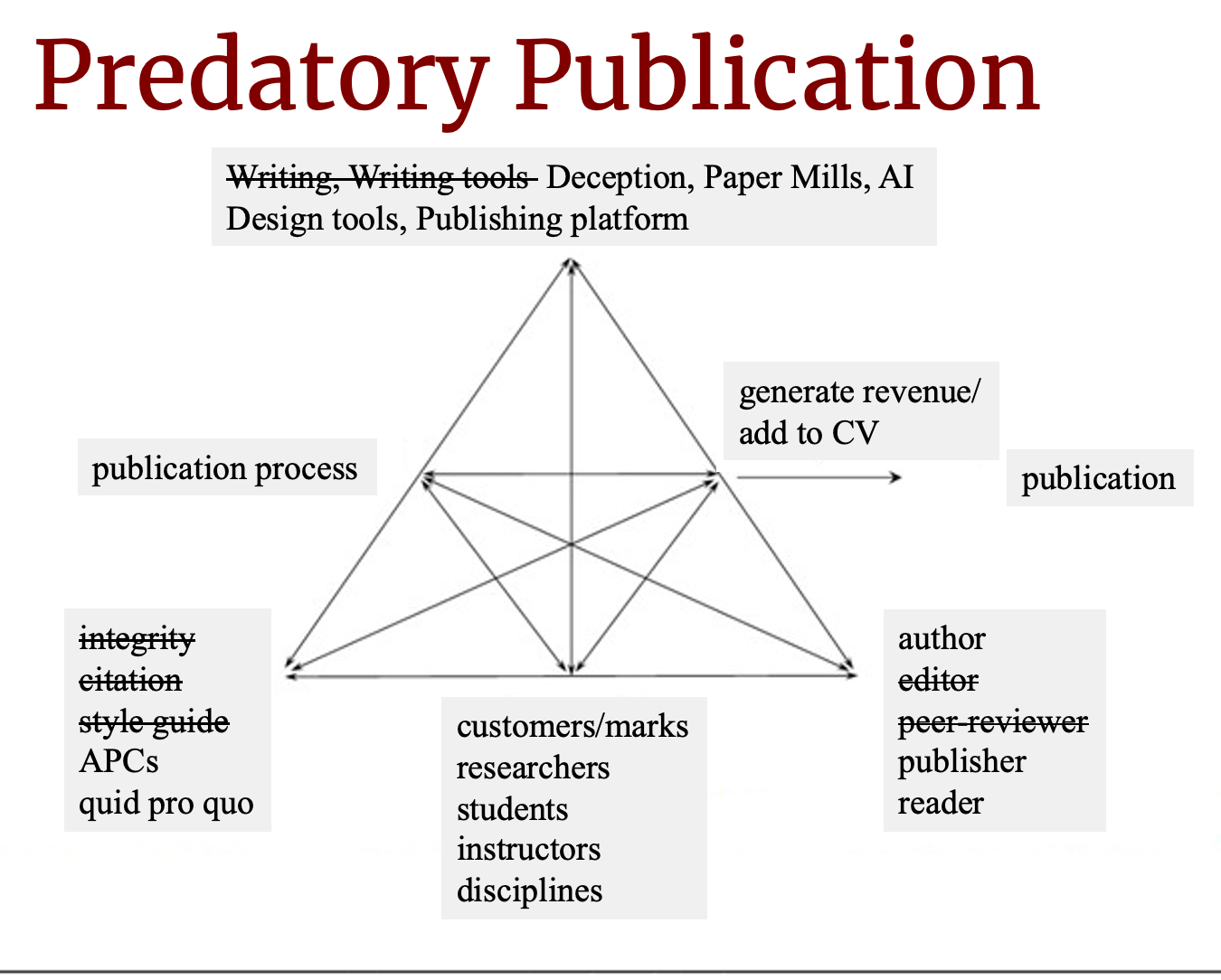
Predatory publications are not concerned with writing quality (or even coherence), and thus also do not care about writing tools (although we could, perhaps, include generative AI as a tool that replaces those used by human authors). The rules change pretty radically as the predatory version does away with nearly all of the rules in our legitimate academic publishing model and replaces them with rules related to paying for publication (via article processing charges, listed as APCs in the model), and replacing the ethical framework from one of acknowledgment and indebtedness to a capitalist quid pro quo—a pay-to-play model.
The division of labor no longer includes editors (at least in terms of individuals who perform editing; there are individuals listed as editors but their main purpose is to facilitate the transaction of money for publication). Similarly, the object of the publication is solely career advancement (on the part of the author) and profit making (on the part of the publisher); advancement of knowledge is no longer a concern.
Predatory publishing is a problem for all academic researchers and scholars (although it appears more prevalent in STEM fields). The development of generative AI applications has made it far easier for unscrupulous actors to create fake journals and to populate both fake and legitimate journals with fictional research that sounds appropriately crafted, as the grammar and mechanics are quite good.
We'll have another post later on AI in publishing, as it has implications for all of us. For now, there are not many good options for combatting predatory publishing aside from helping scholars understand what it is and how to avoid contributing to it. We also combat it by developing and running legitimate journals that feature strong peer review and ethical treatment of both authors and editors, which we hope is an easy position for our readers to sign on to.
How to Avoid Predatory Publishing?
You don't need Beall's List. You may want to check a brand new (and hilariously titled) journal called Reviews: The Journal of Journal Reviews, started by a bunch of really smart and thoughtful librarians who understood and disagreed with the take-down approach of Beall's List and wanted to create a more careful way of analyzing journals on their publishing practices.
You might also refer to the Directory of Open-Access Journals, which we will discuss in more detail in a later post. And you can also use Think, Check, Submit, which provides a free, downloadable checklist that allows you to cross-check the credibility and viability of a journal yourself! Don't fall into the fear-hole of predatory publishing!
In our next post, we we're going to talk about how the role of open-access journals and predatory publishing plays into the misconceptions of journal editors, as they worry about starting or migrating to open-access or digital-only journals.
References
Cook, Florence Govender Roganie, & Brennan, Peter A. (2023). Greetings from your predatory journal! What they are, why they are a problem, how to spot and avoid them. British journal of oral and maxillofacial surgery 61(3), 245-247. https://doi.org/10.1016/j.bjoms.2023.02.005
Engeström, Yrjö. (1987). Learning by expanding: An activity-theoretical approach to developmental research. Orienta-Konsultit Oy.
Fisher, Laura, Nugent, Nicola, & Pendlebury, Anna (2022). Detecting and preventing paper mill publications at the Royal Society of Chemistry. Eon, 15(8). https://eon.pubpub.org/pub/zeapf0tc/release/1
McAvinia, Claire. (2016). Online learning and its users: Lessons for higher education. Chandos Publishing.
Schiavo, Renata (2020, Nov. 7). What are predatory journals? How not to fall into their trap and why they exist. https://ludwig.guru/blog/covid-19-push-scooters-and-predatory-journals/
Teixeira da Silva, Jaime A. (2020). An alert to COVID-19 literature in predatory publishing venues. Journal of Academic Librarianship, 46(5). https://doi.org/10.1016/j.acalib.2020.102187